We have published and presented this paper at the 26th Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN). DOI: https://doi.org/10.1109/ICIN56760.2023.10073509
ABSTRACT:
Software-Defined Networking (SDN) is a new paradigm in network architecture that improves scalability, flexibility, control, and network management by separating the control plane from the data plane. SDN controllers have a global view of the entire network and provide the ability to dynamically change traffic forwarding rules. However, Introducing SDN
brings some new DDoS attack vulnerabilities, such as limited flow table capacity and single point failure of a controller.
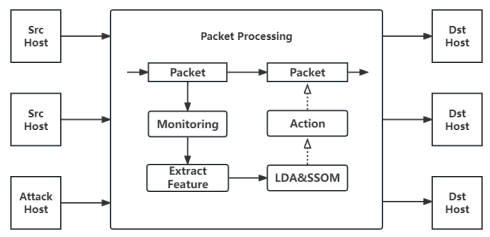
This paper proposes an approach that combines linear discriminant analysis (LDA) and a supervised self-organizing map (SOM) called LSSOM that enables to detecting suspicious packets to defend against DDoS attacks in real-time. Our experimental results show that using LSSOM achieves 98.2% accuracy and reduces the classification time by 73.5% compared to using supervised SOM only.